Server Virtualization: Explained to the Business Administration Professional
High-Level Overview of Server Virtualization:
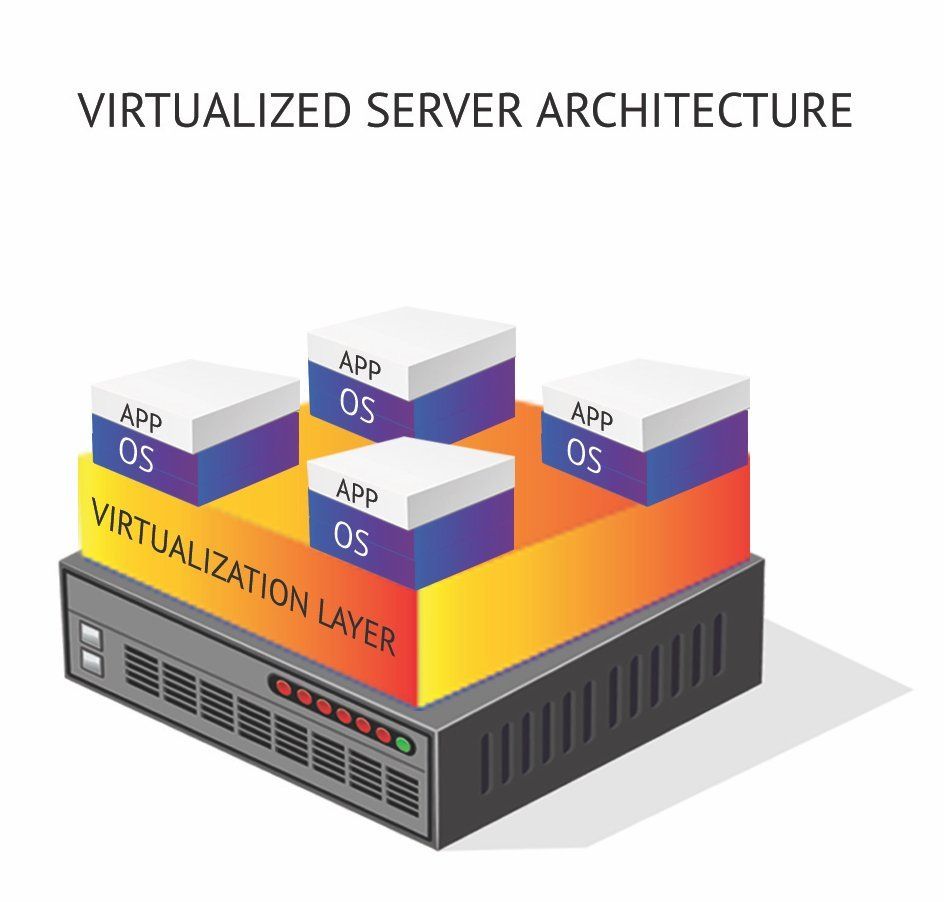
Within the virtualized server environment illustrated below, there are four virtual servers or virtual machines (VMs). Each of these VMs run different operating systems and can reside on the same physical host. This is possible because VMware’s hypervisor software serves as an operating system that’s capable of allocating the host’s storage, memory and compute resources among the various virtual machines running on top of it. The virtual machines will run their respective operating systems and applications.
Business Reasons for Virtualizing Servers:
Reduce Capital Expenditures
By virtualizing your servers, you can eliminate the amount of hosts needed within your infrastructure.
Reduce the Risk of Costly Downtime
If using VMware’s vSphere Standard Edition or higher, you can create real-time replication within your infrastructure. For example, a workflow running on a host that has crashed can seamlessly boot on another host without experiencing downtime.
It’s more time efficient servicing virtual machines than physical hosts. These efficiencies are made possible by VMware’s vCenter management tool that provides high visibility into the server environment while simplifying the patching and provisioning processes. Additionally, you’ll need less rack space within your datacenter and can reduce utility expenses by requiring less energy for cooling.
Contact us to help plan your virtualized server architecture.
written by:
Brendan Kelly
Brendan Kelly is a Business Alliance Manager focused on building partnerships with technology companies that can help The Walker Group’s clients increase efficiencies, reduce operating expenses and mitigate IT security risks. Prior to assuming the Business Alliance Manager role at Walker, Brendan spent 10+ years in new business sales and account management roles while working for both software and service providers.
WE ARE PROUD TO BE
More Recent News